Journey Cloud Sync's End-to-end Encryption - What Is it & How Does It Work?
At Journey, we keep our user's privacy and the safe-keeping of their journal entries a priority. In line with these efforts, we will be introducing end-to-end encryption in Journey Cloud Sync, an asymmetric encryption designed to be secure and verifiable by users. Read on to find out more.
Data security and privacy has been at the top of our priority list at Journey. With every new update and improvement to our platform, we have made it a point to make sure that our users continue to feel safe and secure using our platform to journal.
In line with these efforts, we have been working on implementing end-to-end encryption into Journey's new cloud sync, the Journey Cloud Sync Drive. With standard asymmetric end-to-end encryption protocols and technologies being put in place, journal entries and images can be further protected and kept private in the platform, allowing our users to continue to feel safe using Journey.
Read on to find out more about how end-to-end encryption works on Journey.
What is End-to-End Encryption?
End-to-end encryption is a security measure that ensures that data transmitted between two parties remains encrypted and protected from unauthorized access throughout the entire process. It is a method of encrypting information in such a way that only the owner of the data can decrypt and read it.
The main advantage of end-to-end encryption is that it provides a high level of security and privacy. It is commonly used in various applications and services, including messaging apps, voice and video calls, and file sharing platforms, to provide users with enhanced security and privacy for their data or content.
Since the information is encrypted on the user's device and can only be decrypted by the owner of the content, even the service providers facilitating the cloud sync cannot access or read the content. This ensures that sensitive information, such as journals, personal thoughts, memories, and media files remain confidential and protected from unauthorized access.
How does End-to-End Encryption work in Journey Cloud Sync?

With end-to-end encryption on Journey, our goal is for our users' personal journaling content to be encrypted on their device and protected before it is uploaded to Journey's servers. We designed the end-to-end encryption to be asymmetric. Asymmetric encryption uses two different but related keys for encryption and decryption; a public key and a private key, and it relies on these keys to ensure data security and privacy.
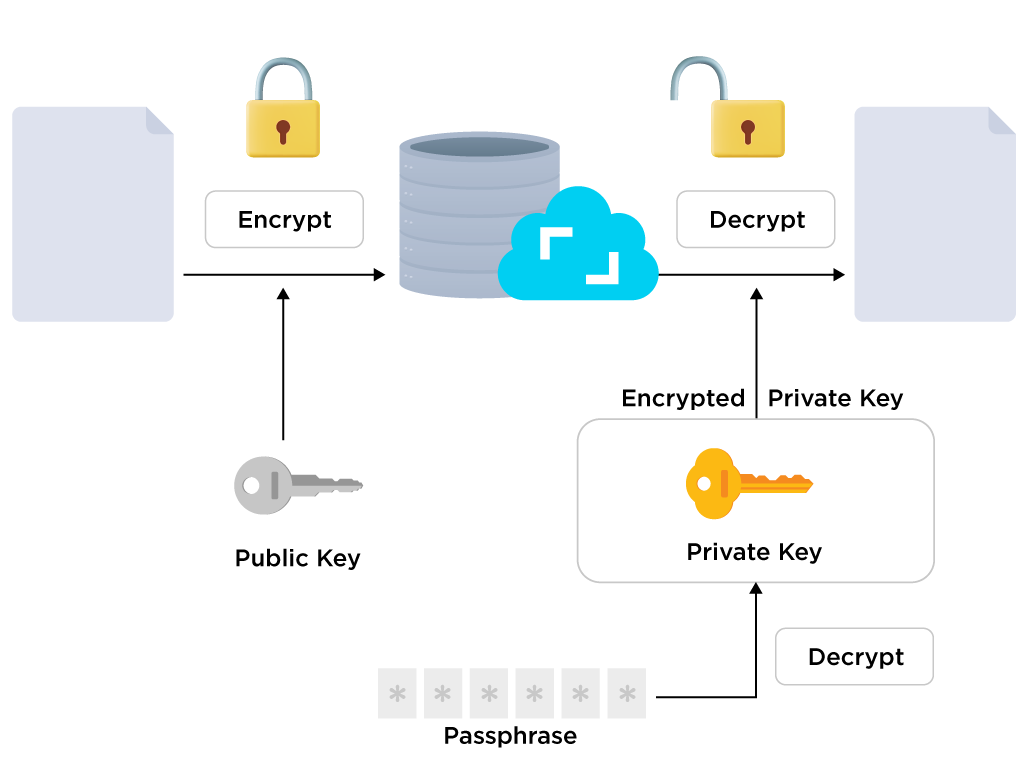
Here's how end-to-end encryption works:
1. Encryption: When a journal entry is uploaded from an encrypted drive, the content in the entry is encrypted on the user's device through the RSA, or Rivest–Shamir–Adleman encryption algorithm that encrypts the original text in the journal entry into an unintelligible form, or ciphertext.
End-to-end encryption in Journey Cloud Sync utilizes the public key to encrypt sensitive information before they are sent to Journey's servers.
2. Transmission: During transmission, the encrypted content is then transmitted over a network, such as the internet. Even if the content is intercepted or accessed by unauthorized individuals or entities, it remains in its encrypted form and cannot be deciphered and read without the passphrase and private key. The content is further protected by HTTPS during transmission.
3. Decryption: When the user wishes to access their journal entries again, the encrypted content is downloaded to the user's device and decrypted using both the encrypted private key sent from Journey's server and the passphrase which is required to be input by the user.
4. Key Management: Journey users will safekeep their passphrase. The public key and the encrypted private key are managed safely in Journey's server. This way, users do not have to share their passphrase or private key with Journey or anyone else in order to use the Journey Cloud Sync.
1. Setting up End-to-End Encryption in Journey Cloud Sync
When the user adds a Journey Cloud Sync Drive, they will be prompted to turn on end-to-end encryption and add a passphrase to secure their drive.
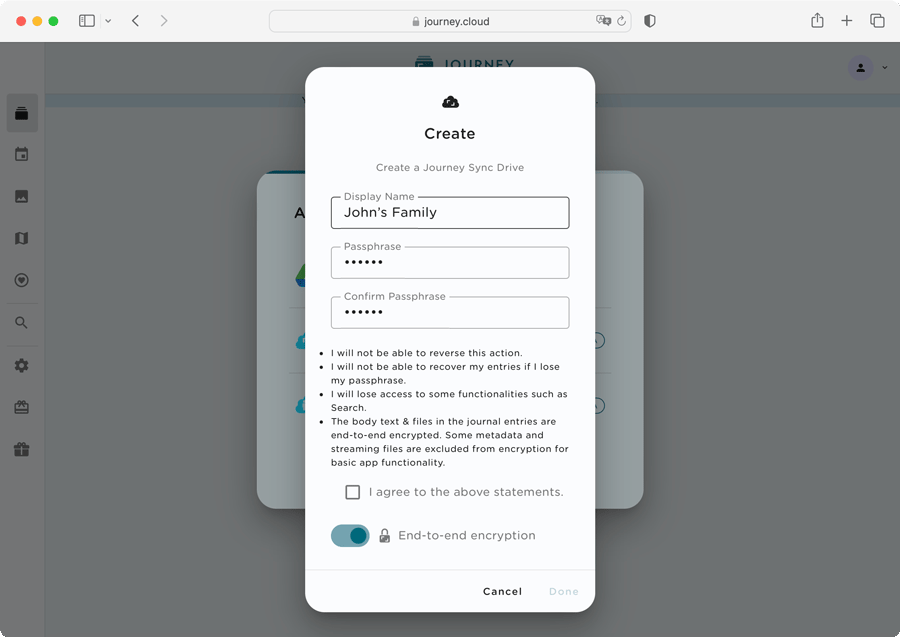
When users choose to turn on end-to-end encryption, it initiates a process that secures their journal entries and is irreversible. A public-private key pair will be generated randomly in the front end. The users will be required to input a passphrase which will be used to encrypt the private key. The public and encrypted private key will then be stored in the Journey's server. The private key will be destroyed at the end of this process.
2. Encrypting Journal Entries & Media Files
When users create and save an entry, the content of the journal entries gets encrypted in the front end using the user's public key. The content passes through the RSA encryption algorithm to turn from normal text into ciphertext. The encrypted text will then be uploaded into Journey's cloud, ensuring that even if intercepted, the encrypted journal content remains secure and unreadable.
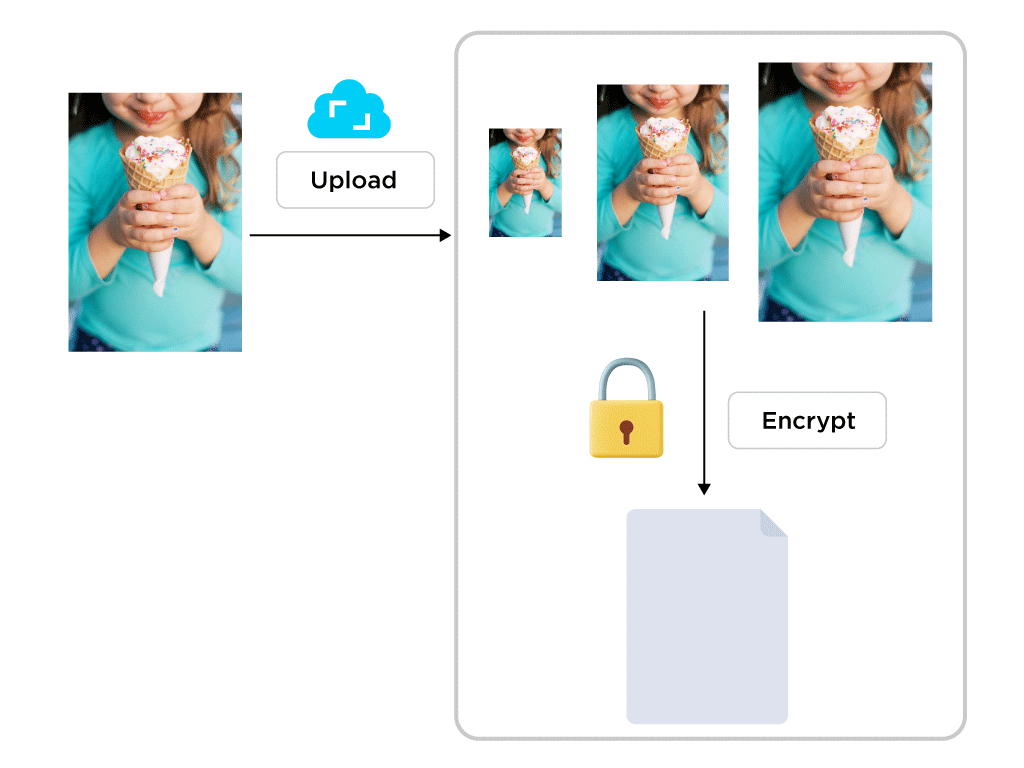
When users upload image, video and audio files into a journal entry, Journey would need to process the media files first. For example, Journey will generate different variations of the images such as the thumbnails. For audio/video files, an M3U8 playlist will be generated and the video/audio will be broken into smaller chunks in order to facilitate online streaming. Due to the technical limitations to achieve this in the front end, the original media files would be sent to the cloud to be processed first before encrypting.
Since RSA encryption is only able to encrypt data to a maximum amount equivalent to the key size, it is impractical to encrypt media files with RSA directly. As such, the media files are encrypted using symmetric encryption. When a media file is uploaded to Journey, a unique shared key will be generated to encrypt the media files using AES, or Advanced Encryption Standard encryption algorithm. The shared key will then be encrypted with the public key. At the end of this process, the shared key will be destroyed. The original image, audio and video files cached in the Journey's server will also be destroyed immediately. Only the encrypted media files and the encrypted shared key are stored in Journey Cloud Sync.
3. Decrypting Journal Entries & Media Files
When users wish to access their journal entries, the encrypted entries will be sent from the Journey server to the front end. Users would be required to input their passphrase in order to decrypt the journal entries.
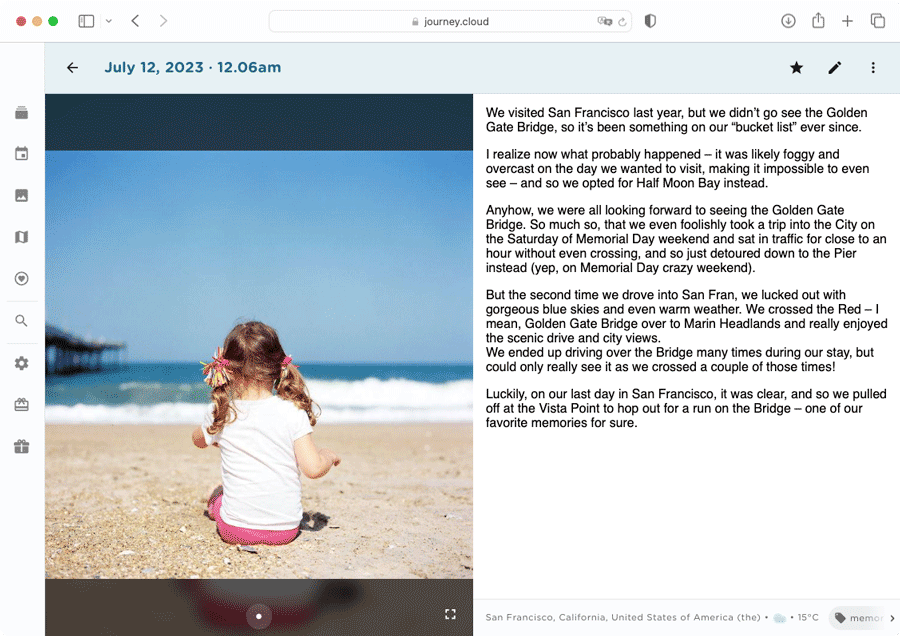
Decryption works when the users' passphrase decrypts the encrypted private key into a private key. The private key is then put through the RSA decryption algorithm to decrypt the encrypted content into the original content. The original content is then delivered to the user's device and displayed securely on the browser or app.
When the app fetches the user's media files, the server will deliver the encrypted files to the front end. The encrypted shared key of the media files will be decrypted by the private key. With the shared key, the app will be able to decrypt the encrypted media files into the original content before displaying them securely on the browser or app.
Verifying End-to-End Encryption in Journey Cloud Sync
Journey Cloud Sync follows the end-to-end encryption protocols very closely to ensure that our users' journal entries and media are safekept and protected on our platform. With end-to-end encryption, we have made as little compromise as possible, while considering other aspects such as the user experience and the app's functionality.
Anyone should be able to verify that the end-to-end encryption processes work in Journey and that their journal entries are encrypted safely without leaving room for the possibility of anyone accessing them in the back end.
Here are some ways users can verify that the end-to-end encryption on Journey Cloud Sync is functioning as intended:
1. Verifying End-to-End Encryption in Journey Cloud Sync During Setup
When users create a Journey Cloud Sync Drive, users can verify that only the public key and the encrypted private key are transmitted to our servers by inspecting it in the network. Neither the private key nor the passphrase are sent to our back end.
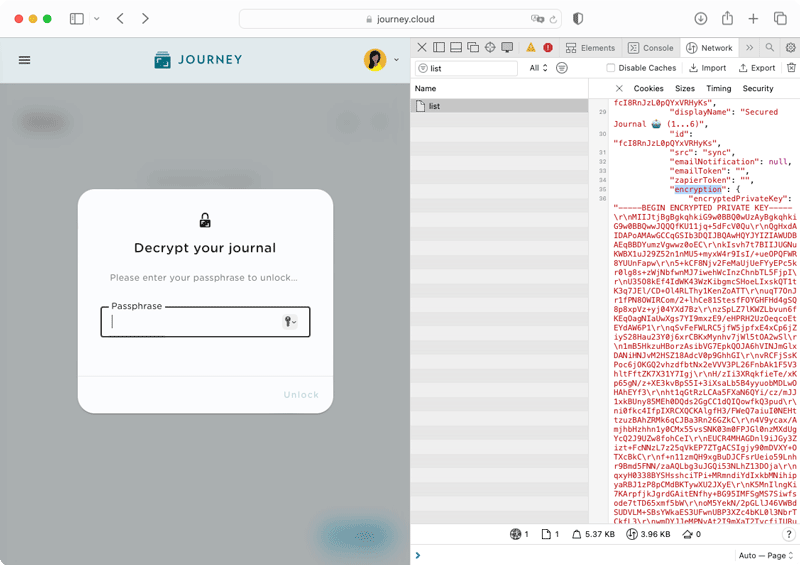
As shown in the network preview, only the public key and the encrypted private key are sent over the network, while their passphrase and private key are not. This verification will make clear that no one except you can read your journal entries in the back end without your passphrase or private key.
2. Verifying Encrypting Process For Journal Entries & Media Files
When a user creates a journal entry, the texts of their journal entry will be encrypted using the public key. The journal entry will then be stored in our servers as encrypted text, or ciphertext.
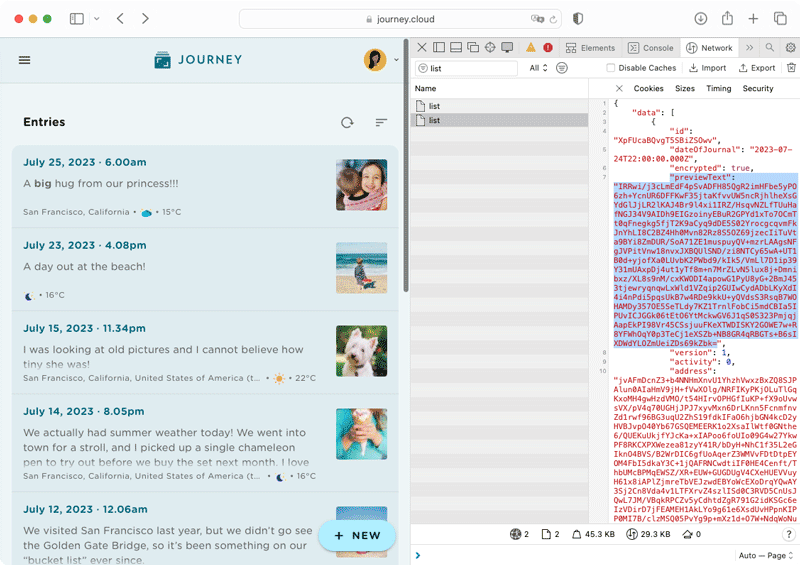
This can also be verified by inspecting the network of the web browser. As shown in the network preview, the text and the preview text are displayed in ciphertext and in an unreadable format. This demonstrates that their content has been successfully encrypted before sending over to the Journey's server. Since Journey Cloud Sync does not store the passphrase in the server, there is no way for anyone to decrypt the content in the back end.
As the media files are sent to Journey's server to be processed before encrypting, users can only verify that the media files are encrypted in the back end during decryption.
3. Verifying Decrypting Process For Journal Entries & Media Files
When users access to their encrypted drive, the passphrase would be required to decrypt the content of the journal entries. Users can verify that only the encrypted private key and the public key are being fetched from the back end against the network activities shown in the browser.
As shown in the network preview, only the encrypted private key and the public key have been fetched from the back end Journey servers.
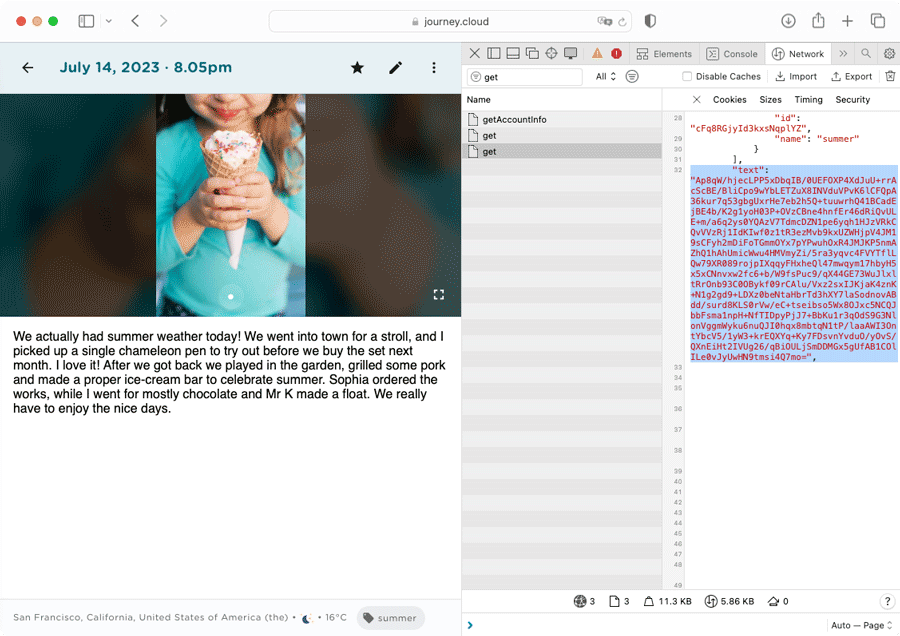
Users can also verify that the encrypted texts and media files are indeed encrypted in Journey's cloud by checking against the individual entry from the list of entries in the network preview. For the audio/video files, user can verify that that the video/audio chunks are encrypted by downloading the chunks and stitching all the files found in the M3U8 playlist together into a single audio/video file. The audio/video should reflect as encrypted, and they should not be able get back the original audio/video.
Users can be assured that the next place where the original texts and media files are shown decrypted would be in the front end.
Limitations of End-to-End Encryption
While one's personal journaling content belongs to solely them and the encrypted body text and the media files of their entries are stored in the server, some meta data is excluded from this for the app's basic functionality, such as the display name of the drive, and the date and time that journal entries are created.
It is important to note that this action cannot be reversed if end-to-end encryption is turned on, and that journal entries and data would be lost if the passphrase is lost.
Users will also not be able to use the Search function on Journey if they choose to turn on end-to-end encryption, as this prevents Journey from indexing their journal entries.
With this new update, we will be continuing to work on evolving and strengthening our encryption measures over time. As we gather feedback from our users and run further tests, we will also be keeping in mind to preserve the compatibility and functionality of the Journey platform.
When designing the Journey Cloud Sync, we follow the asymmetric end-to-end encryption protocols very closely to ensure that the encryption and decryption processes run smoothly and securely. Users can also verify if the content in their journal entries are being encrypted by checking the network activities shown in the browser on their own accord.
We hope that end-to-end encryption in Journey Cloud Sync provides greater assurance and confidence to our users on the Journey platform. We are also committed to ensure a secure journal platform and better privacy protection for our users in the long run.